Set up Browser Isolation
Browser Isolation is enabled through Secure Web Gateway HTTP policies. By default, no traffic is isolated until you have added an Isolate policy to your HTTP policies.
Setup instructions vary depending on how you want to connect your devices to Cloudflare. Refer to the links below to view the setup guide for each deployment option.
| Connection | Mode | Description |
|---|---|---|
| Gateway with WARP | In-line | Apply identity-based HTTP policies to traffic proxied through the WARP client. |
| Access | In-line | Apply identity-based HTTP policies to Access applications that are rendered in a remote browser. |
| Gateway proxy endpoint | In-line | Apply non-identity HTTP policies to traffic forwarded to a proxy endpoint. |
| Magic WAN | In-line | Apply non-identity HTTP policies to traffic connected through a GRE or IPsec tunnel. |
| Clientless remote browser | Prefixed URL | Render web pages in a remote browser when users go to https://<your-team-name>.cloudflareaccess.com/browser/<URL>. |
To configure Browser Isolation policies:
- In Zero Trust ↗, go to Gateway > Firewall Policies > HTTP.
- Select Add a policy and enter a name for the policy.
- Use the HTTP policy selectors and operators to specify the websites or content you want to isolate.
- For Action, choose either Isolate or Do not Isolate.
- (Optional) Configure settings for an Isolate policy.
- Select Create policy.
Next, verify that your policy is working.
Users can see if a webpage is isolated by using one of the following methods:
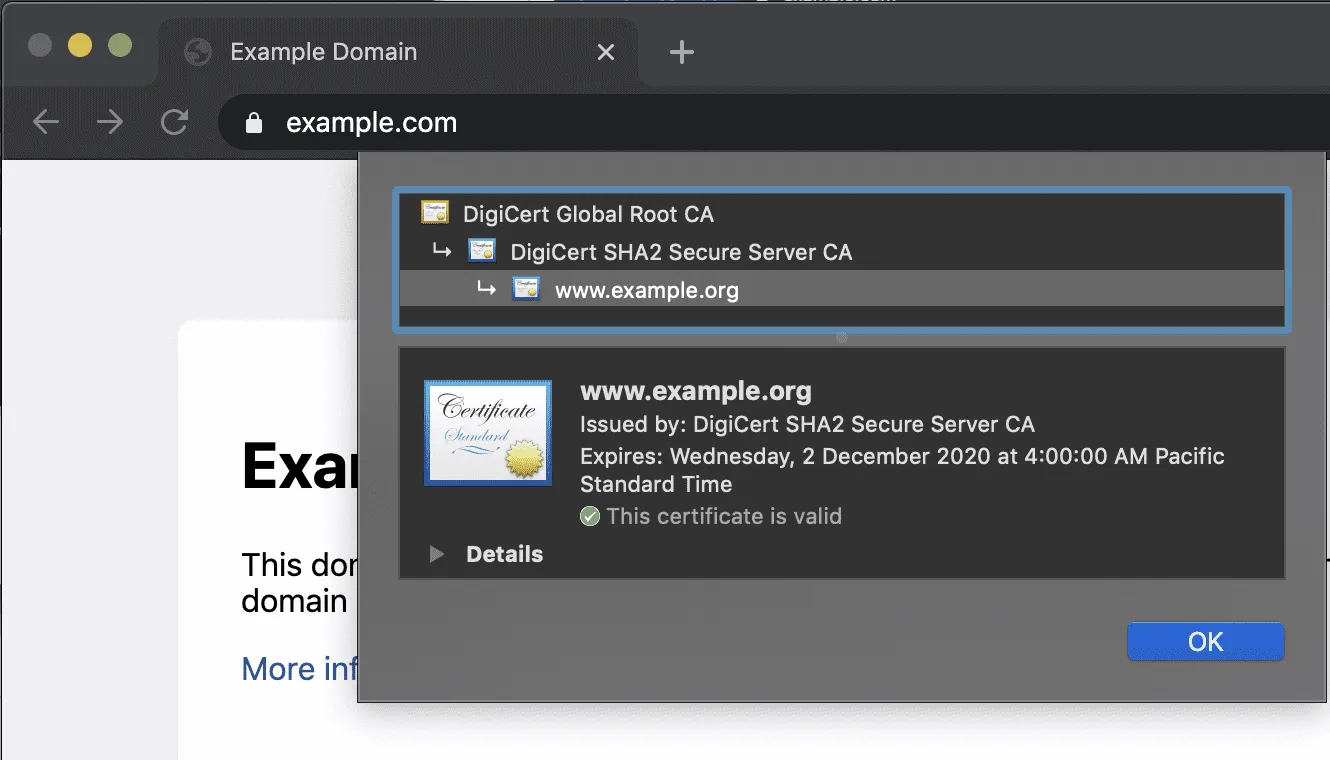
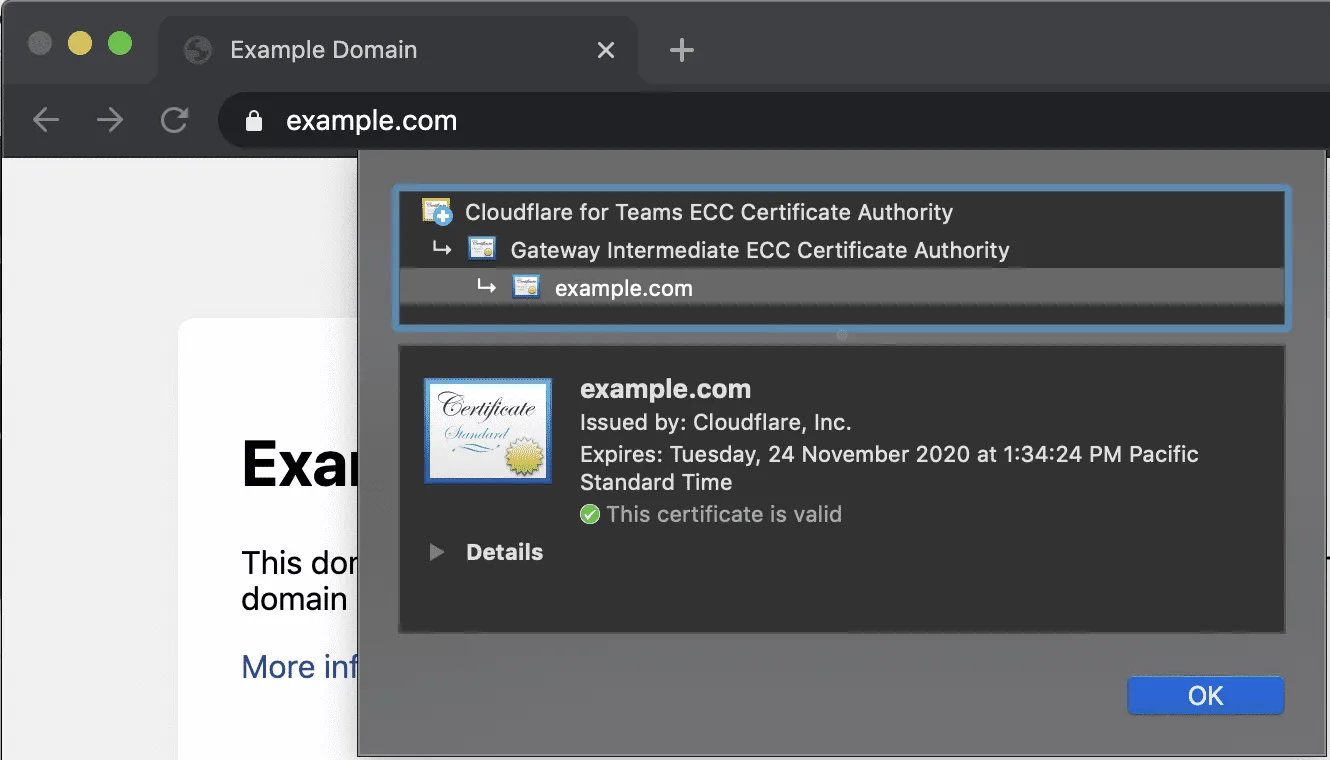
- Select the padlock in the address bar and check for the presence of a Cloudflare Root CA.
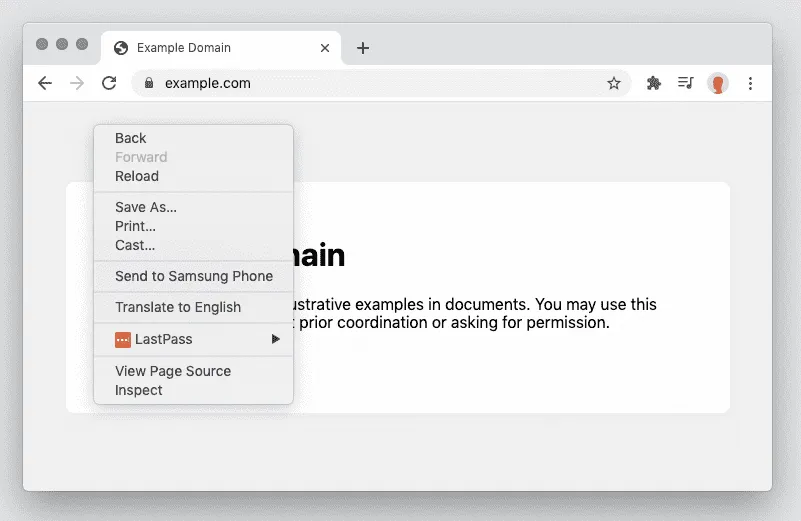
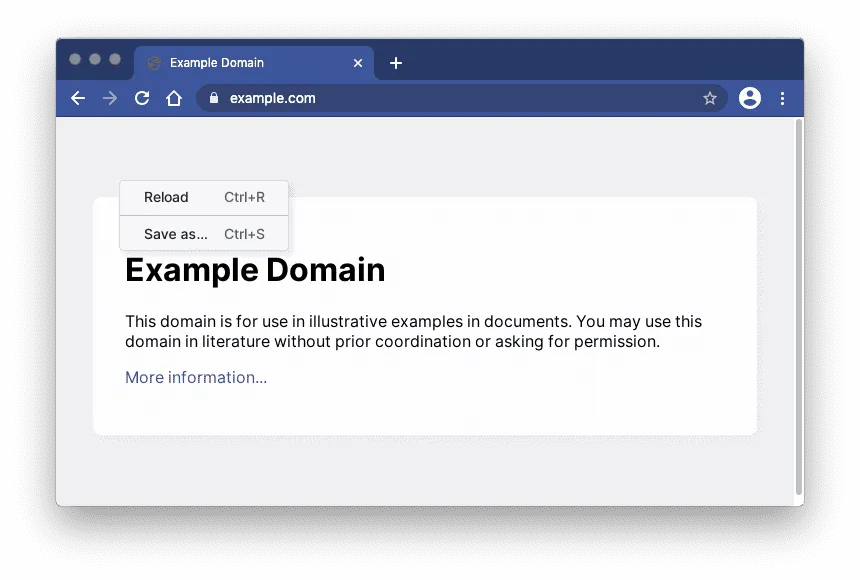
- Right-click the web page and view the context menu options.
-
A non-Cloudflare root certificate indicates that Cloudflare did not proxy this web page.
-
The right-click context menu will have all of the normal options.
-
A Cloudflare root certificate indicates traffic was proxied through Cloudflare Gateway.
-
The right-click context menu will be simplified.
WARP users can temporarily disable remote browsing by disconnecting the WARP client. Once WARP is disconnected, a refresh will return the non-isolated page.